Our Security Process
Product Supply Chain
Lenovo's product supply chain has been recognized in Gartner's Top 25 rankings the past three years. It plays a critical role in the development, manufacture, and delivery of our products. The supply chain begins with the management and control of a qualified supplier base, which provides qualified and secure components for use in development and manufacturing.
Critical, large volume components are tracked via barcodes, and
controlled in the supplier’s inventory and assembly process
until receipt at Lenovo. Manufacturing takes place in a secure,
controlled environment, including a secure physical facility, and
a secure network. Completed products are then packaged with
tamper-evident seals for boxes and pallets. Shipments are then
tracked from origin to customer delivery.
The diagram below shows the complete product life cycle. The
Supply Chain involves the areas identified as Suppliers, and
Lenovo Manufacturing and Test.
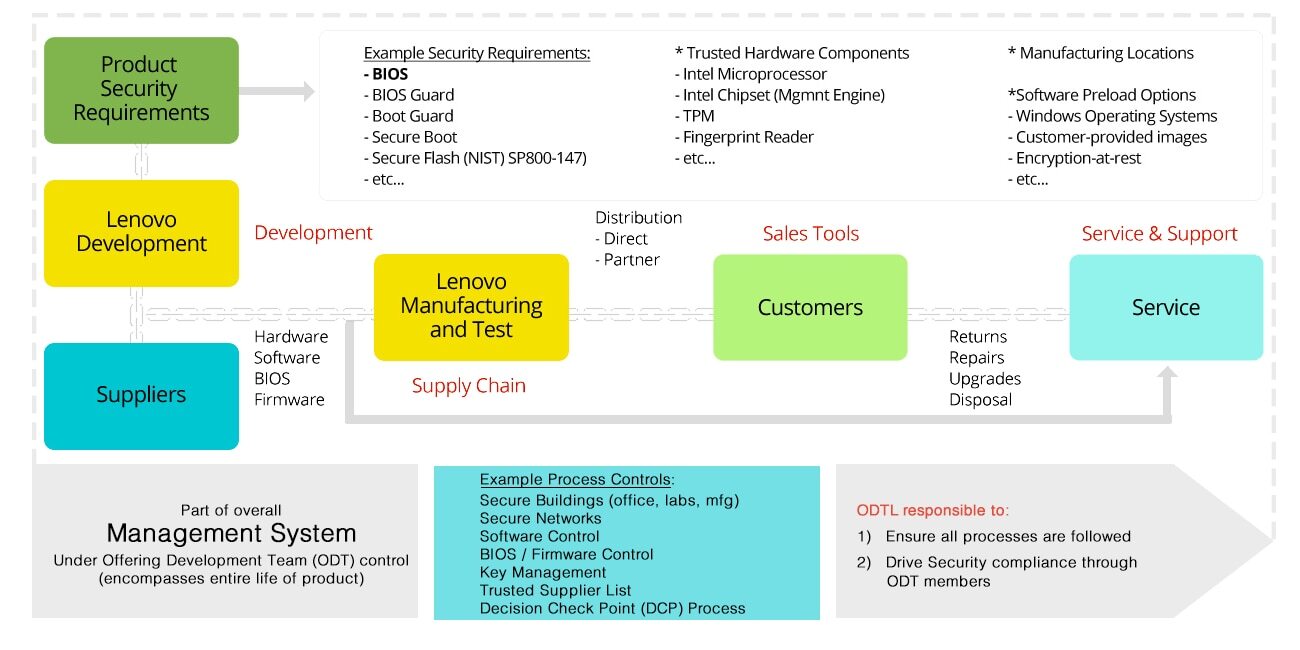
In addition, there is technical work required to support the product throughout its life. Once the product is shipped, there is typically a need to qualify components to replace any end-of-life (EOL) parts, as well as a need to provide BIOS/firmware updates through a secure process. These are part of the overall Life Cycle Management and Support of the product.
Product Planning and Development involves many areas throughout the product life cycle. Planning activity begins by defining security requirements when products are first being conceived In order to balance needs of security and data availability. Enhancements are in process to include ongoing review and improvements to critical secure development processes through which the products are designed and tested. Once the security requirements are documented, Lenovo’s product development teams establish plans to incorporate appropriate features into the new products. The Development phase focuses on the following areas:
- Development and Qualifications
- BIOS/Firmware
- Software
Supplier Management & Control
A strong supplier base in the product supply chain –
including ODMs, OEMs, component manufacturers, BIOS and software
providers -- is critical to the success of any technology device
maker. To help ensure this, Lenovo has a process for qualifying
its core suppliers, and then formally evaluating them on a
quarterly basis. Many Lenovo suppliers have been its partners for
over 20 years. These relationships are carefully managed and new
suppliers are thoroughly assessed.
Lenovo has enhanced our supplier relationships through a Trusted
Supplier Program. The goal of the program is
management of customer risk through the implementation of a
documented and auditable supply chain security program as one part
of the total product security process. The Trusted Supplier
Program focuses on suppliers of intelligent components,
ODM’s, OEM’s, and repair service providers that could
impact customer security.
Intelligent components include:
- Any software or firmware program on any microprocessor,
- The microprocessor itself,
- Any semiconductor device that has data processing ability,
- Any component or device that has internal memory,
- Any component or device that performs an input/output function
Lenovo proactively and continually reviews its sourcing
requirements to ensure that we keep up with - and stay ahead of -
trends and vulnerabilities as they arise in the technology
marketplace.
Lenovo’s work to ensure the security of its products and
supply chain has been recognized by Chain Security, LLC, one of
the leading security firms in the United States. This conclusion
comes after almost three years of detailed study into
Lenovo’s security processes, corporate governance and
supplier programs. The result of this analysis is a 20-page Letter
of Attestation in which Chain Security details their work with
Lenovo, the changes and improvements Lenovo has made in the last
two years and Chain Security’s conclusion that Lenovo
“is likely ahead of the industry” in terms of these
security processes.
To read the full letter, click
here.
Risk Management
Lenovo relies on its global supply chain to help design, build, and deliver technology solutions our customers can trust. Strategically, there are five key areas/steps that we follow in managing risks to the supply chain:
- Identify potential risks to the supply chain;
- Protect Lenovo’s supply chain with special controls;
- Detect issues early, giving more time and options with which to respond;
- Respond as quickly as possible to mitigate any threats; and
- Recover with minimal disruption to customers by designing a supply chain that is resilient.
To fulfill this strategy, Lenovo constantly keeps its supply chain systems evaluated, updated, and optimized to meet customer and business needs.
- Lenovo regularly audits our suppliers and vendors for compliance, security, and financial health. For critical components, there will be an assessment on the need for multiple suppliers (or multiple supplier manufacturing sites).
- Lenovo also closely monitors internal processes, testing the strength of our controls on a regular basis.
Any circumstance that impacts our ability to meet our
customers’ needs must be monitored, analyzed, and managed -
and eventually mitigated. By identifying issues early, Lenovo can:
- Adjust supply chains to minimize impact
- Work with suppliers to address issues
- Replace supplier if issues remain unresolved
Minimizing risk for both Lenovo and its customers in the supply chain is critical.
Secure Manufacturing
A secure manufacturing site requires the following:
- Physical security: strong practices and controls manage the security of personnel and physical plants. This includes access controls, and monitoring of visitors and deliveries.
- Secure manufacturing processes: inside manufacturing areas, production processes and controls are closely managed, while major components and subassemblies are tracked electronically. Final products are inspected, and then tested to confirm they meet security, reliability, and functionality requirements.
- Secure software imaging and BIOS distribution: customer imaging (i.e. the pre-installation of customer selected OS and other application software) and BIOS setup are sensitive steps in the manufacturing process; Lenovo takes extra precautions to keep these protected from any kind of outside tampering.
Secure Logistics
Lenovo logistics covers packaging, shipping, and delivery. Once the products are built and tested, they are packaged and prepared for shipping with tamper-evident materials so that any problems can be noticed immediately and in route, and the incident investigated. After packaging, Lenovo works with qualified logistics suppliers to safely deliver products to end customers. Protection throughout the shipping process includes secure facilities, trucks and conveyances, and thoroughly-screened employees, visitors, and drivers. Shipments are tracked from the time they leave Lenovo buildings until they are received at a customer's location.
Lifecycle Management
Lenovo's commitment to security continues well after products are
delivered to customers. Operating system and applications
software, chipsets, firmware, and BIOS can have frequent updates
from Lenovo as well as its ecosystem suppliers,including phone
carriers. These updates can be scheduled improvements, or
they can be in response to work done by the PSIRT to fix a
security vulnerability. Whatever the reason, Lenovo has processes
in place for the
secure delivery of software updates and componentry throughout the
life of the product, even in instances when suppliers may have
ended production of components being used in Lenovo systems. This
creates a need to qualify new parts that can be used for service.
Lenovo is committed to source replacement parts from suppliers on
the Trusted Supplier List.